Nortel VPN Router
Contents
- 1 Platform Notes
- 2 Version History
- 3 Backoff Patterns
- 4 Vendor IDs
- 5 Authentication Methods
- 6 ISAKMP SA Lifetime
- 7 Transform Attribute ordering and re-writing
- 8 Aggressive Mode
- 9 Response to Noncompliant and Malformed Packets
- 10 NAT Traversal
- 11 IVEv2
- 12 Remote Access VPN Client
- 13 Other Interesting Behaviour
- 14 Default Configuration
- 15 Discovered Vulnerabilities
Platform Notes
The Nortel VPN router uses a proprietary operating system that runs on proprietary hardware. The operating system is based on VxWorks, and the hardware is based on an Intel CPU with a PC motherboard.
The Nortel VPN router was previously known as Nortel Contivity. It was originally a Bay Networks product, called Bay Networks Enterprise Switch. This Bay Networks name can still be seen in the Vendor ID that starts with the letters BNES.
Version History
| Version | Release Date | Notes |
|---|---|---|
| V04_85 | ||
| V04_90 | ||
| V05_00 | ||
| V05_05 | ||
| V06_00 | ||
| V06_05 |
Backoff Patterns
The Nortel VPN router has the four-packet backoff pattern:
0, 16, 16, 16
This backoff pattern is the same for all software versions that I have tested. Below is an example from a Contivity 1600 running software version V06_00.310:
$ ike-scan -M --showbackoff 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=0af98bad8d200783)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
IKE Backoff Patterns:
IP Address No. Recv time Delta Time
192.168.124.152 1 1171799005.325513 0.000000
192.168.124.152 2 1171799021.346876 16.021363
192.168.124.152 3 1171799037.380750 16.033874
192.168.124.152 4 1171799053.414670 16.033920
192.168.124.152 Implementation guess: Nortel Contivity
Vendor IDs
The Nortel VPN router doesn't send any Vendor IDs in Main Mode unless the initiator sends a Vendor ID packet. It doesn't matter what VID the initiator sends; it just has to send something.
Below is an example showing this behaviour:
$ ike-scan -M 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=a9516e7f6f5340c8)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
$ ike-scan -M --vendor=00 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=2aca7e13cf8ee7e9)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
VID=424e45530000000a (Nortel Contivity)
If the initiator sends a main mode request with a Vendor ID payload, the Nortel VPN router will respond with the Nortel Contivity Vendor ID. This consists of the string BNES (hex 424e4553) followed by a 32-bit big-endian value. BNES stands for Bay Networks Enterprise Switch, which gives an insight to the legacy of this product. The 32-bit value appears to be a version number, but I do not know the exact mapping. I have observed values 00000004, 00000005, 00000007, 00000009 and 0000000a.
Authentication Methods
The Nortel VPN router supports Pre-Shared Key and RSA Signature authentication methods. By default, both of these methods are enabled.
The examples below show a Nortel VPN router running software version V06_05.135 responding to Pre-Shared Key and RSA Signature authentication methods.
$ ike-scan -M --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=9c80d5553c1764cc)
SA=(Enc=DES Hash=SHA1 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
$ ike-scan -M --trans=1,2,3,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=6f4b867e0288bf3f)
SA=(Enc=DES Hash=SHA1 Auth=RSA_Sig Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
ISAKMP SA Lifetime
Lifetime in Seconds
The Nortel VPN router allows no lifetime in seconds, or any non-zero value from 1 to the maximum that can be represented in 4 bytes. It does not allow a value of zero or a variable length attribute with a value length greater than four bytes, in both cases it will return NO-PROPOSAL-CHOSEN.
$ ike-scan -M --lifetime=none --trans=1,2,1,1 192.168.124.152 Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=dfbf6c7a2f54467d)
SA=(Enc=DES Hash=SHA1 Auth=PSK Group=1:modp768)
$ ike-scan -M --lifetime=0 --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=fe076896a7e24094)
$ ike-scan -M --lifetime=1 --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=e7678a9a9e66d143)
SA=(Enc=DES Hash=SHA1 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00000001)
$ ike-scan -M --lifetime=0xffffffff --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=f3444d274ccff275)
SA=(Enc=DES Hash=SHA1 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0xffffffff)
$ ike-scan -M --lifetime=0x0000000000000001 --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=a8a5feba533c004d)
Lifetime in Kilobytes
The Nortel VPN router does not support a lifetime in kilobytes for the ISAKMP SA, and always returns NO-PROPOSAL-CHOSEN if one is specified.
$ ike-scan -M --lifetime=none --lifesize=0 --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=2d5d0747f3b68bd2)
$ ike-scan -M --lifetime=none --lifesize=1 --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=459aab1087c26c35)
$ ike-scan -M --lifetime=none --lifesize=1000 --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=60aafe6517f85fb5)
$ ike-scan -M --lifetime=none --lifesize=0xffffffff --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=4bdd62eff10118f4)
Transform Attribute ordering and re-writing
Nortel Contivity generally returns the transform attributes in the order that they are supplied by the initiator.
In the example below, we specify the four mandatory transform attributes in order Enc, Hash, Auth, Group and then in reverse order Group, Auth, Hash, Enc, and observe that in both cases the target returns the attributes in the same order as the initiator specified them.
$ ike-scan -M --trans="(1=1,2=2,3=1,4=1)" 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=14395bb3dc072aed)
SA=(Enc=DES Hash=SHA1 Auth=PSK Group=1:modp768)
$ ike-scan -M --trans="(4=1,3=1,2=2,1=1)" 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=f4617f8492037abf)
SA=(Group=1:modp768 Auth=PSK Hash=SHA1 Enc=DES)
Here is another example, this time including a lifetime in seconds. Again, the attributes are returned in the same order that the initiator sent them.
$ ike-scan -M --trans="(11=1,12=12345,4=1,3=1,2=2,1=1)" 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=fdb0408c7d573059)
SA=(LifeType=Seconds LifeDuration=12345 Group=1:modp768 Auth=PSK Hash=SHA1 Enc=DES)
Aggressive Mode
The Nortel VPN router supports IKE aggressive mode.
Here is a simple aggressive mode response, with no client ID specified.
$ ike-scan -A -M --trans=1,2,1,1 --dhgroup=1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Aggressive Mode Handshake returned
HDR=(CKY-R=98e1ce1a384b510c)
SA=(Enc=DES Hash=SHA1 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
KeyExchange(96 bytes)
Nonce(20 bytes)
ID(Type=ID_IPV4_ADDR, Value=192.168.124.152)
Hash(20 bytes)
Response to Noncompliant and Malformed Packets
The examples below are from software version 6.05
No acceptable transforms
$ ike-scan -M --trans=2,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=249165333597ad6b)
Bad IKE version
$ ike-scan -M --trans=1,2,1,1 --headerver=0x30 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Notify message 5 (INVALID-MAJOR-VERSION)
HDR=(CKY-R=37cd960d926d266f)
$ ike-scan -M --trans=1,2,1,1 --headerver=0x11 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Notify message 6 (INVALID-MINOR-VERSION)
HDR=(CKY-R=7f73b228982e696c)
Invalid DOI
$ ike-scan -M --doi=2 --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Notify message 2 (DOI-NOT-SUPPORTED)
HDR=(CKY-R=8950c773a1379ce5)
Invalid Situation
$ ike-scan -M --situation=2 --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Notify message 3 (SITUATION-NOT-SUPPORTED)
HDR=(CKY-R=64112f25a9e9b475)
Invalid Initiator Cookie
Nortel VPN router ignores an invalid cookie, or perhaps it considers a zero initiator cookie as valid.
$ ike-scan -M --cookie=0000000000000000 --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=f5fa02b7ec7d2ded)
SA=(Enc=DES Hash=SHA1 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
Invalid Flags
Strangely, Nortel VPN router reports INVALID-COOKIE rather than INVALID-FLAGS.
$ ike-scan -M --hdrflags=255 --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Notify message 4 (INVALID-COOKIE)
HDR=(CKY-R=8d8fadb5c075528b)
Invalid Protocol
Nortel VPN router reports NO-PROPOSAL-CHOSEN rather than INVALID-PROTOCOL-ID.
$ ike-scan -M --protocol=2 --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=23c56761f7369896)
Invalid SPI
$ ike-scan -M --spisize=32 --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=28717ef5119e1c3c)
SA=(Enc=DES Hash=SHA1 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
Non-Zero Reserved Fields
$ ike-scan -M --mbz=255 --trans=1,2,1,1 192.168.124.152
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=d7488c1ec9313143)
SA=(Enc=DES Hash=SHA1 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
NAT Traversal
The Nortel VPN router supports NAT Traversal. There are three settings:
- NAT Traversal enabled or disabled (default is disabled)
- Disable Client IKE Source Port Switching (default is not selected)
- UDP port (no default, Nortel recommend port 10001)
I have not been able to get the Nortel VPN router to respond to ike-scan with NAT Traversal.
The command line entries that control NAT traversal are:
ipsec nat-traversal port 4500 no ipsec nat-traversal ipsec nat-traversal client-ike-source-port-switching enable
IVEv2
The Nortel VPN Router does not support IKEv2 as of software version 6_05.
Remote Access VPN Client
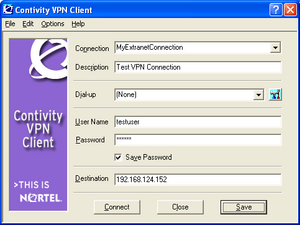
The Nortel VPN Router uses the Nortel VPN Client. The screenshot on the right shows version V06_01.014 of this client.
The table below shows the transforms offered by the Nortel client using username/password authentication without an initial group authentication. With this authentication scheme, the client uses IKE Aggressive Mode.
| No. | Encryption | Hash | Authentication | DH Group | Other attributes |
|---|---|---|---|---|---|
| 1 | AES/256 | SHA1 | PSK | 8 (EC2N 283) | 32767=26 |
| 2 | AES/128 | SHA1 | PSK | 8 (EC2N 283) | 32767=26 |
Note the use of the elliptic curve Diffie-Hellman group 8, and the use of the proprietary transform attribute 32767 with value 26.
Other Interesting Behaviour
Default Configuration
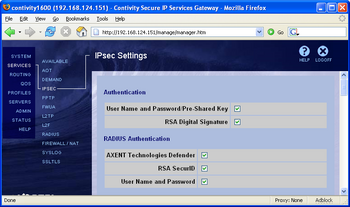
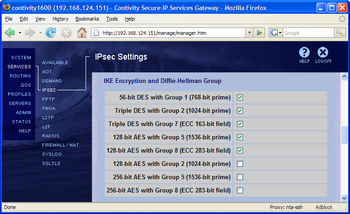
The screenshot on the right shows the default settings in the web-based GUI, and the config file excerpt below shows the default settings in command-line mode.
ipsec authentication local username-password ipsec authentication local rsa-sig ipsec authentication radius axent-defender ipsec authentication radius dynamic-securid ipsec authentication radius username-password
ipsec encryption ike des56-group1 ipsec encryption ike 3des-group2 ipsec encryption ike 3des-group7 ipsec encryption ike 128aes-group5 ipsec encryption ike 128aes-group8 no ipsec encryption ike 128aes-group2 no ipsec encryption ike 256aes-group8 no ipsec encryption ike 256aes-group5
Note that the Weak DES with DH Group 1 is offered by default.
Also note that the ECC Diffie-Hellman groups 7 and 8 are supported, and are enabled by default in some transforms.