Ike-scan Frequently Asked Questions
Contents
What does "cannot bind to port 500" mean?
This means either:
- You don't have privilege to bind to low ports; or
- Another process has already bound this port.
The text after the Could not bind message tells you which of these problems it is, and the sections below give details of each of them.
Insufficient Privileges
ERROR: Could not bind network socket to local port 500 You need to be root, or ike-scan must be suid root to bind to ports below 1024. ERROR: bind: Permission denied
This means that you don't have sufficient privileges to bind to low ports (below 1024). On most systems, you need to be root (superuser) to do this. By default, ike-scan uses UDP port 500 as the source port, which requires root privileges to bind to.
Possible solutions are:
- Run ike-scan as root (login as root, become root with su, or run the command as root with sudo);
- Install the ike-scan binary SUID root; or
- Use the --sport option to specify a high source port instead.
Installing ike-scan SUID root may introduce a security risk if it contains exploitable bugs. I am not aware of any such bugs, and I have taken care to avoid them, but there are no guarantees.
Using --sport to specify a port above 1023 does not work for all VPN servers, because some will only respond to source port 500. If you want to use a random high source port, you can use --sport=0.
Another Process is Using the Port
ERROR: Could not bind network socket to local port 500 Only one process may bind to the source port at any one time. ERROR: bind: Address already in use
This means that another process on the system has already bound to port 500. This may be another instance of ike-scan, or an IKE server process.
Possible solutions are:
- Stop the other process that has bound to UDP port 500; or
- Use the --sport option to specify an alternative source port.
To identify the other process, look for processes called things like ike, ipsec or isakmp. You may also be able to use netstat to track the process down.
Using --sport to specify an alternative source port does not work for all VPN servers, because some will only respond to source port 500. If you want to use a random high source port, you can use --sport=0.
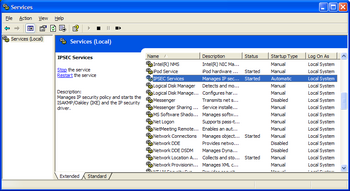
The screenshot on the right shows the Windows XP IPsec service, which is an example of a process that binds to UDP port 500. To run ike-scan on Windows XP you need to stop this service or use a different source port.
If I double-click ike-scan.exe under Windows, a window appears but closes immediately
ike-scan and its associated programs are command line utilities. You must run them from the command line, not from a GUI environment.
To run ike-scan under windows first launch a command prompt window, typically cmd.exe, then run ike-scan. If the directory containing ike-scan is not in your path, then you will need to specify the full path or change directory to the folder containing ike-scan.
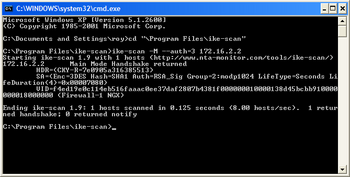
The screenshot on the right shows ike-scan running on Windows XP using the cmd.exe command prompt.
ike-scan is sending DNS requests for ike-scan-target.test.nta-monitor.com
The short answer is: upgrade to ike-scan version 1.9 or later.
The long answer is: this was due to the following debugging code that was included in ike-scan.c up to and including version 1.8:
if (!no_dns_flag)
hp = gethostbyname("ike-scan-target.test.nta-monitor.com");
This DNS lookup code did not change the operation of ike-scan, but it could introduce a delay on systems with no working DNS.
This code was never required for public use, and was removed from the code in version 1.9.
Why do I get a response if I scan the local host?
If you scan the host that you are running ike-scan from, you will receive a response that makes it appear that it is running an IKE listener. This is misleading; what is actually happening is that ike-scan is receiving it's own IKE packet and displaying it as if it were a response.
Here is an example:
$ ike-scan -M 127.0.0.1
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
127.0.0.1 Main Mode Handshake returned
HDR=(CKY-R=0000000000000000) (8 transforms)
Note that the responder cookie is non-zero, which is indicative of an IKE request packet as responses will normally have non-zero responder cookies (although some implementations do return zero responder cookies under certain conditions). Also there are eight transforms in the proposal, and a response packet will only have a single transform.