Symantec Raptor Firewall
Contents
- 1 Platform Notes
- 2 Version History
- 3 Backoff Patterns
- 4 Vendor IDs
- 5 Authentication Methods
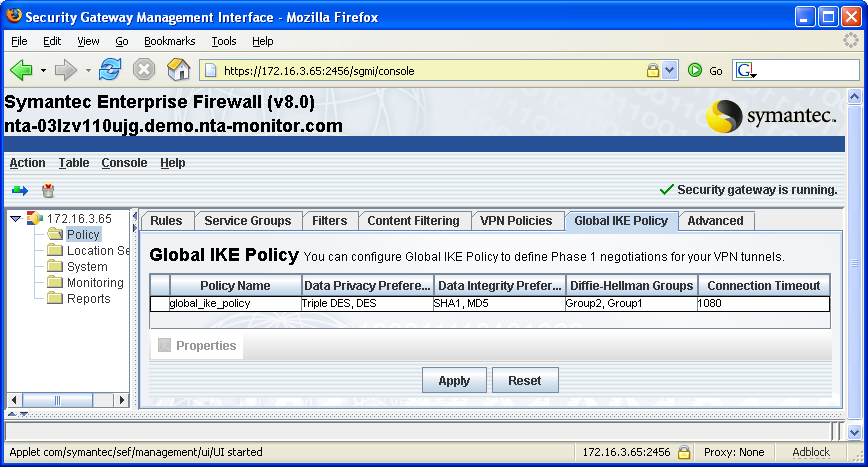
- 6 ISAKMP SA Lifetime
- 7 Transform Ordering and Rewriting
- 8 Aggressive Mode
- 9 Response to Noncompliant and malformed packets
- 10 NAT Traversal
- 11 IKEv2
- 12 Remote Access VPN Client
- 13 Other Interesting Behaviour
- 14 Default Configuration
- 15 Discovered Vulnerabilities
- 16 Misc stuff
Platform Notes
The raptor firewall was originally developed by Raptor Systems. Raptor Systems were acquired by Axent technologies in December 1997, and Axent Technologies were themselves acquired by Symantec in July 2000.
The VPN component is called PowerVPN.
Version History
Backoff Patterns
$ ike-scan -M --showbackoff 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Main Mode Handshake returned
HDR=(CKY-R=04efd542f7187e91)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=2:modp1024 LifeType=Seconds LifeDuration=28800)
VID=526170746f7220506f77657256706e20536572766572205b56382e315d (Symantec-Raptor-v8.1)
IKE Backoff Patterns:
IP Address No. Recv time Delta Time
172.16.3.65 1 1174832876.239420 0.000000
172.16.3.65 2 1174832881.615095 5.375675
172.16.3.65 3 1174832890.248545 8.633450
172.16.3.65 Implementation guess: UNKNOWN
172.16.3.65 1 1174832971.144670 0.000000 172.16.3.65 2 1174832980.550190 9.405520 172.16.3.65 3 1174832995.239567 14.689377
172.16.3.65 1 1174833091.855363 0.000000 172.16.3.65 2 1174833101.288213 9.432850 172.16.3.65 3 1174833115.954724 14.666511
Vendor IDs
Symantec Raptor sends the following Vendor ID in both main and aggressive mode:
- 526170746f7220506f77657256706e20536572766572205b56382e315d ("Raptor PowerVpn Server [V8.1]")
The Vendor ID is the ASCII string Raptor PowerVpn Server [V8.1], which ike-scan displays as hex.
Authentication Methods
Symantec Raptor only appears to support Pre-Shared Key authentication for IKE Phase-1.
Here is an example of a Symentec Enterprise Firewall version 8.0 responding to a main mode request using pre-sherad key authentication:
$ ike-scan -M 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Main Mode Handshake returned
HDR=(CKY-R=e4f67307ce556c7b)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=2:modp1024 LifeType=Seconds LifeDuration=28800)
VID=526170746f7220506f77657256706e20536572766572205b56382e315d (Symantec-Raptor-v8.1)
ISAKMP SA Lifetime
Lifetime in Seconds
Symantec Raptor supports any lifetime in seconds for IKE Phase-1, including no lifetime at all. If the lifetime in seconds is supplied as a variable-length attribute, it must be encoded in four bytes, otherwise Raptor will respond with BAD-PROPOSAL-SYNTAX.
$ ike-scan -M --lifetime=none --trans=5,2,1,2 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Main Mode Handshake returned
HDR=(CKY-R=c2e01058b40532c6)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=2:modp1024)
VID=526170746f7220506f77657256706e20536572766572205b56382e315d (Symantec-Raptor-v8.1)
$ ike-scan -M --lifetime=0 --trans=5,2,1,2 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Main Mode Handshake returned
HDR=(CKY-R=77a6050bdbe73f8c)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=2:modp1024 LifeType=Seconds LifeDuration=0)
VID=526170746f7220506f77657256706e20536572766572205b56382e315d (Symantec-Raptor-v8.1)
$ ike-scan -M --lifetime=1 --trans=5,2,1,2 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Main Mode Handshake returned
HDR=(CKY-R=86da7aa2f1e15af9)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=2:modp1024 LifeType=Seconds LifeDuration=1)
VID=526170746f7220506f77657256706e20536572766572205b56382e315d (Symantec-Raptor-v8.1)
$ ike-scan -M --lifetime=0xffffffff --trans=5,2,1,2 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Main Mode Handshake returned
HDR=(CKY-R=f4b1085a10672f23)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=2:modp1024 LifeType=Seconds LifeDuration(4)=0xffffffff)
VID=526170746f7220506f77657256706e20536572766572205b56382e315d (Symantec-Raptor-v8.1)
$ ike-scan -M --lifetime=0xffffffffffffffff --trans=5,2,1,2 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Notify message 15 (BAD-PROPOSAL-SYNTAX)
HDR=(CKY-R=fb0a3c6d79f757a9, msgid=5b395b10)
Lifetime in Kilobytes
Symantec Raptor does not accept a lifetime in kilobytes for IKE Phase-1. If one is specified, it will respond with NO-PROPOSAL-CHOSEN. If both lifetime in kilobytes and lifetime in seconds is specified, then it will respond with BAD-PROPOSAL-SYNTAX.
$ ike-scan -M --lifetime=none --lifesize=0 --trans=5,2,1,2 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=8e44801b703a5ce4, msgid=b493f32b)
$ ike-scan -M --lifetime=none --lifesize=1 --trans=5,2,1,2 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=69645fb452685755, msgid=77cefaae)
$ ike-scan -M --lifetime=none --lifesize=1000 --trans=5,2,1,2 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=1cca5f141fa98fb5, msgid=4b012e20)
$ ike-scan -M --lifetime=none --lifesize=100000 --trans=5,2,1,2 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=c13b2156b1619a11, msgid=cfe0b940)
$ ike-scan -M --lifetime=28800 --lifesize=1000 --trans=5,2,1,2 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Notify message 15 (BAD-PROPOSAL-SYNTAX)
HDR=(CKY-R=ff99e7a92127f9cc, msgid=c1308735)
Transform Ordering and Rewriting
Symantec Raptor always returns transform attributes in the order: Enc, Hash, Auth, Group [,Lifetime in Seconds] regardless of the order in which the attributes were sent by the initiator. Below are some examples illustrating this behaviour:
$ ike-scan -M --trans="(1=5,2=2,3=1,4=2)" 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Main Mode Handshake returned
HDR=(CKY-R=46d8a78157bf230f)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=2:modp1024)
VID=526170746f7220506f77657256706e20536572766572205b56382e315d (Symantec-Raptor-v8.1)
$ ike-scan -M --trans="(4=2,3=1,2=2,1=5)" 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Main Mode Handshake returned
HDR=(CKY-R=42369b81dae6f15f)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=2:modp1024)
VID=526170746f7220506f77657256706e20536572766572205b56382e315d (Symantec-Raptor-v8.1)
$ ike-scan -M --trans="(11=1,12=123,4=2,3=1,2=2,1=5)" 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Main Mode Handshake returned
HDR=(CKY-R=210a927dbc471f5d)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=2:modp1024 LifeType=Seconds LifeDuration=123)
VID=526170746f7220506f77657256706e20536572766572205b56382e315d (Symantec-Raptor-v8.1)
Aggressive Mode
Symantec Raptor supports IKE Aggressive Mode for both site-to-site and remote access VPNs.
Here is an example of a site-to-site VPN responding to IKE aggressive mode. idtype 1 is ID_IPV4_ADDR, and the ID c0a87c07 is the hex representation of the IP address 192.168.124.7.
$ ike-scan -A --idtype=1 --id=0xc0a87c07 -M 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Aggressive Mode Handshake returned
HDR=(CKY-R=49bb214786d4a67f)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=2:modp1024 LifeType=Seconds LifeDuration=28800)
VID=526170746f7220506f77657256706e20536572766572205b56382e315d (Symantec-Raptor-v8.1)
KeyExchange(128 bytes)
Nonce(64 bytes)
ID(Type=ID_IPV4_ADDR, Value=172.16.3.65)
Hash(20 bytes)
Here is an example of a remote access VPN. idtype 11 is ID_KEY_ID, and the ID is the username.
$ ike-scan -M -A --id=test --idtype=11 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Aggressive Mode Handshake returned
HDR=(CKY-R=0de2a1bd4ca99917)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=2:modp1024 LifeType=Seconds LifeDuration=28800)
VID=526170746f7220506f77657256706e20536572766572205b56382e315d (Symantec-Raptor-v8.1)
KeyExchange(128 bytes)
Nonce(64 bytes)
ID(Type=ID_IPV4_ADDR, Value=172.16.3.65)
Hash(20 bytes)
If we specify an unknown user, the VPN server responds with PAYLOAD-MALFORMED. This allows us to enumerate valid users.
$ ike-scan -M -A --id=nosuchuser --idtype=11 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Notify message 16 (PAYLOAD-MALFORMED)
HDR=(CKY-R=373a2cfaa6399eb7, msgid=fda83288)
Response to Noncompliant and malformed packets
The examples below are from Symantec Enterprise Firewall 8.0 running on Windows 2000.
No Acceptable Transforms
$ ike-scan -M --trans=2,1,1,1 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=1d49077b1a1cb246, msgid=5a056542)
Bad IKE version
No response.
$ ike-scan -M --headerver=0x30 172.16.3.65 Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/) Ending ike-scan 1.9.1: 1 hosts scanned in 2.476 seconds (0.40 hosts/sec). 0 returned handshake; 0 returned notify
$ ike-scan -M --headerver=0x11 172.16.3.65 Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/) Ending ike-scan 1.9.1: 1 hosts scanned in 2.474 seconds (0.40 hosts/sec). 0 returned handshake; 0 returned notify
Invalid DOI
$ ike-scan -M --doi=2 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Notify message 2 (DOI-NOT-SUPPORTED)
HDR=(CKY-R=f1cd8fcb3ba132ed, msgid=9692fb1e)
Invalid Situation
$ ike-scan -M --situation=2 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Notify message 3 (SITUATION-NOT-SUPPORTED)
HDR=(CKY-R=89262fbe7ef4a2c4, msgid=d50eb453)
Invalid Initiator Cookie
$ ike-scan -M --cookie=0000000000000000 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Main Mode Handshake returned
HDR=(CKY-R=34d315bab8c91d5c)
SA=(Enc=3DES Hash=SHA1 Auth=PSK Group=2:modp1024 LifeType=Seconds LifeDuration=28800)
VID=526170746f7220506f77657256706e20536572766572205b56382e315d (Symantec-Raptor-v8.1)
Invalid Flags
No response.
$ ike-scan -M --hdrflags=255 172.16.3.65 Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/) Ending ike-scan 1.9.1: 1 hosts scanned in 2.472 seconds (0.40 hosts/sec). 0 returned handshake; 0 returned notify
Invalid Protocol
$ ike-scan -M --protocol=2 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Notify message 10 (INVALID-PROTOCOL-ID)
HDR=(CKY-R=d4da3ba444ed6f07, msgid=35a2bf67)
Invalid SPI
$ ike-scan -M --spisize=32 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Notify message 16 (PAYLOAD-MALFORMED)
HDR=(CKY-R=cd02987cf33ad6c0, msgid=7380c258)
Non-Zero Reserved Fields
$ ike-scan -M --mbz=255 172.16.3.65
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
172.16.3.65 Notify message 16 (PAYLOAD-MALFORMED)
HDR=(CKY-R=5f2c9899feccb923, msgid=39441803)
NAT Traversal
IKEv2
Symantec Raptor does not support IKEv2 as of Enterprise Firewall version 8.0, and does not respond to IKEv2 requests.
$ ike-scan -M --ikev2 172.16.3.65 Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/) Ending ike-scan 1.9.1: 1 hosts scanned in 2.469 seconds (0.41 hosts/sec). 0 returned handshake; 0 returned notify